OAuth 2.0 Common
Overview
Open Authorization 2.0 (OAuth 2.0) is an authentication and authorization framework that allows third-party applications limited access to HTTP services and authorization of third-party applications on behalf of consenting users, by means of various grants. In this article, we will go through everything you need to know to link AppsAnywhere to an OAuth 2.0 service for single sign-on.
AppsAnywhere uses the Authorization Code grant type, where an authorization code is exchanged for an access token once the user has provided consent. This access token will then typically contain the identity information required to authenticate the user and authorize them for use of AppsAnywhere.
AppsAnywhere currently supports OAuth 2.0 with two providers:
Azure Active Directory (described by OAuth 2.0 Azure )
Active Directory Federation Services (described by OAuth 2.0 ADFS )
It is recommended you follow these guides first to ensure set up is complete on the provider side, and that you have the information necessary to then configure the SSO method within AppsAnywhere.
For most providers you will need to specify a return URL when configuring OAuth 2.0. As you will have not yet configured AppsAnywhere, it is a good idea to think of a "URL Identifier" ahead of time so you can provide the full and correct return URL during the set up.
For example if your site was located at https://myappsanywhere.com and you wanted your URL identifier to be my-oauth, then the resulting return URL would be https://myappsanywhere.com/sso/oauth2/my-oauth
Adding OAuth 2.0 Methods
If you are unfamiliar with the process for adding new SSO methods, steps for doing this and information about common settings associated with all SSO methods can be found on the Single Sign-On Settings page. When selecting which method to add however, be sure to pick from the OAuth 2.0 category, and select the one that corresponds to the provider you are planning to use.
For Azure Active Directory, select the following:
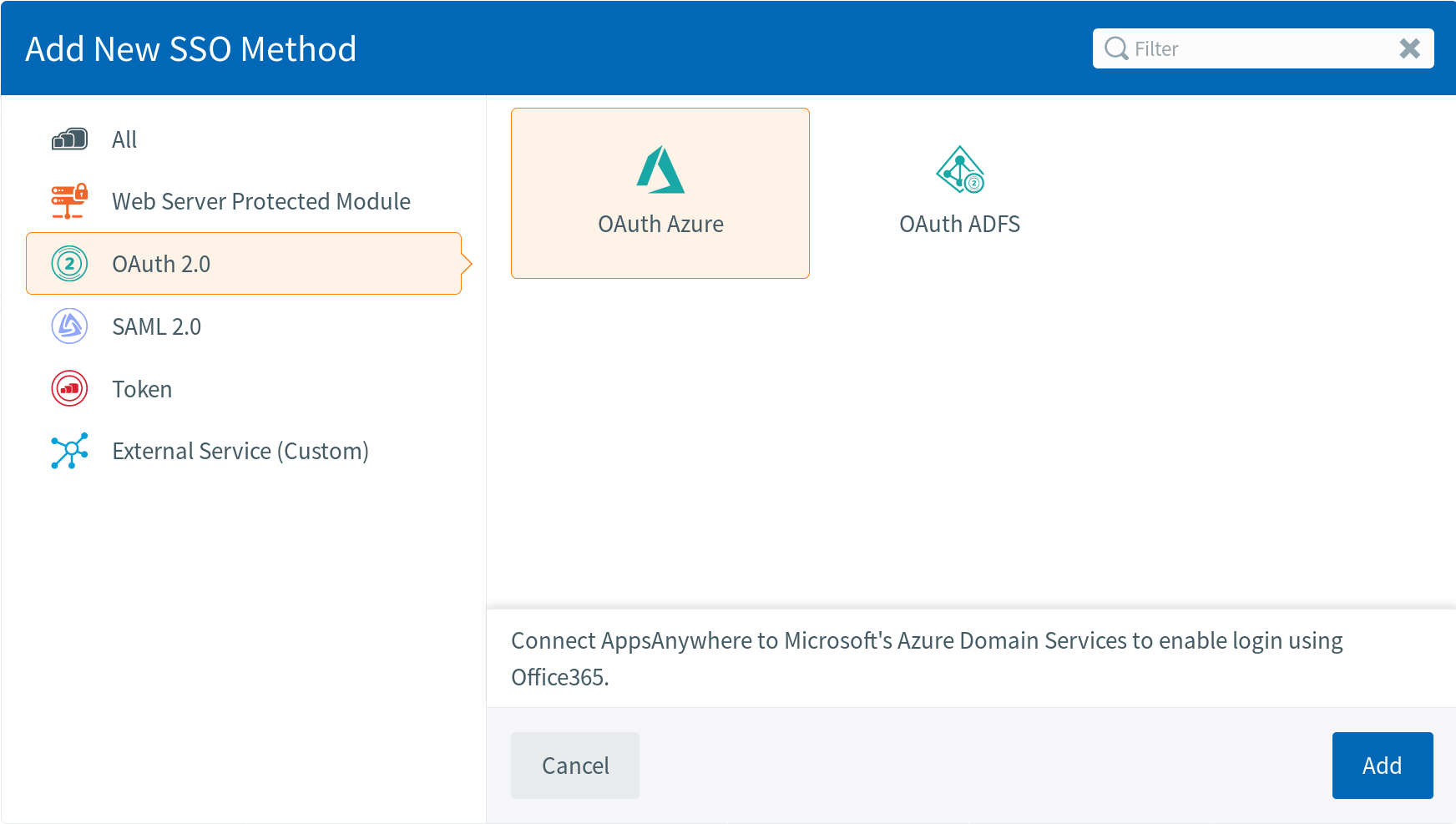
Or for Active Directory Federation Services, select:
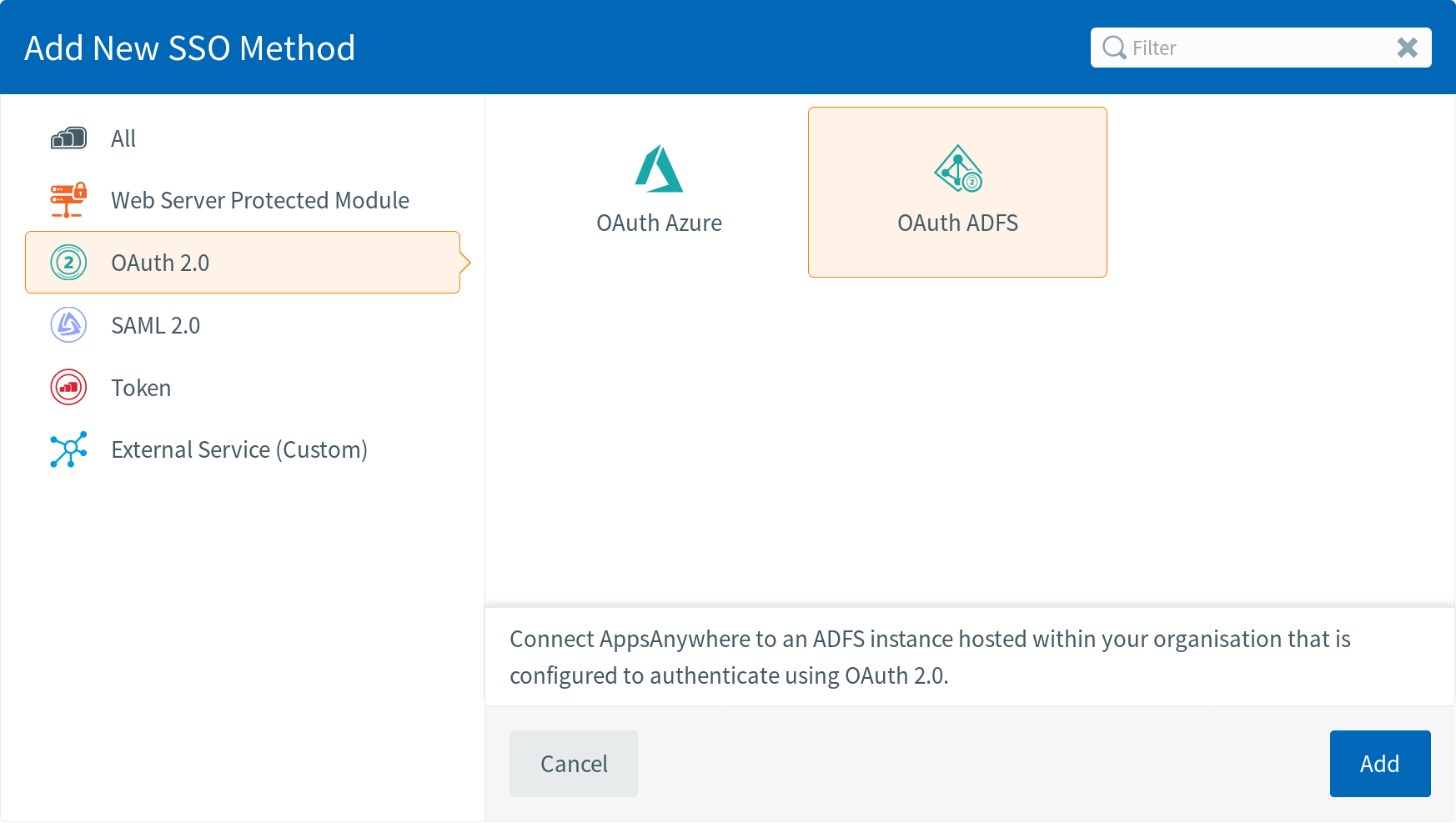
OAuth 2.0 Specific Settings
In addition to the common settings mentioned on the Single Sign-On Settings page, OAuth 2.0 methods include the following:
Field Name | Description | Intended Value |
|---|---|---|
Client ID | The OAuth 2.0 client ID that will either have been generated or supplied by you during the OAuth 2.0 set up of your selected provider. | If supplied by you, make sure it matches exactly. If this is generated by the provider, just make sure you copy it across. |
Client Secret | The OAuth 2.0 secret that will have been generated and given to you during the OAuth 2.0 set up of your selected provider. Although this will not be visible to you when making future edits, it does not need to be supplied every time you save. | As this is generated by the provider, just make sure you copy it across. |
Authentication URL | The base URL of your chosen provider, which paths are appended to when determining each full URL. Example: https://myoauth2endpoint.com[paths-appended-here] | A standard well-formed URL, ideally with no trailing slash, e.g. https://myoauth2endpoint.com For Azure AD, this will typically not need changing from the default. |
Login Path | The base path which will be appended to the authorization URL, forming the main URL used before appending the authentication or token paths. Example: https://myoauth2endpoint.com/example | A URL-compliant URI, ideally with no trailing slash (unless only "/"), e.g. /example This will typically not need changing from the default. |
Authentication Path | The path which will be appended to the main URL (authentication + login), providing the endpoint where OAuth 2.0 authorization requests are sent to. Example: https://myoauth2endpoint.com/example/oauth2/authorize | A URL-compliant URI, ideally with no trailing slash e.g. /oauth2/authorize This will typically not need changing from the default. |
Token Path | The path which will be appended to the main URL (authentication + login), providing the endpoint where OAuth 2.0 token requests are sent to. Example: https://myoauth2endpoint.com/example/oauth2/token | A URL-compliant URI, ideally with no trailing slash e.g. /oauth2/token This will typically not need changing from the default. |
Provider | The selected provider is primarily used by AppsAnywhere to determine the means by which identity information for the authenticating user is retrieved and processed. As OAuth 2.0 (without OpenID) provides standards only for the authentication and authorization of users, each provider is therefore tailor made for retrieving information about the user logging in. | This should match the system you are trying to link AppsAnywhere to, as described earlier. |
Tenant | The tenant ID to use. Allows AppsAnywhere to use the tenant specific login URL rather than the /common URL. This is required if using Azure AD with an oAuth 2.0 application in single tenant mode. If no value is provided AppsAnywhere will use multi-tenant mode. Note: Azure AD Single tenant vs. Multitenant If Single tenant is selected for the App registration in Azure AD, you MUST also enter the correct tenant ID in the ‘Tenent’ field when configurating the oAuth 2.0 connection on AppsAnywhere. If Multitenant is selected for the App registration in Azure AD you MUST NOT enter a value in the ‘Tenent’ field when configurating the oAuth 2.0 connection on AppsAnywhere. | For Azure AD, this should contain the Azure tenant ID to use if the App registration in Azure AD is set to single tenant |
