RDSH Best Practices
Introduction
This article contains AppsAnywhere recommended best practice guidelines for configuring and securing Parallels RAS along with the Microsoft Remote Desktop Services Hosts.
Further details on configuring Parallels RAS can be found in
Remote Desktop Session Hosts
Microsoft Group Policy has a number of configuration settings that can be used in order to restrict and secure access to the RDS hosts. The following options are recommended for a production environment. Time intervals for certain options can be adjusted based on local guidelines or preferences.
Some options also can be set within the Parallels RAS Console. However, both Group Policy and Parallels RAS settings should be configured in tandem to ensure that the correct settings are enforced. This is detailed in the recommendations and configuration steps below.
Gateway Tunneling Policies
Tunneling policies are designed to load balance connections by assigning a group of RD Session Hosts to a specific RAS Secure Client Gateway or RAS Secure Client Gateway IP address.
When tunneling polices are defined and/or enabled they allow native RDP access via MSTSC through the Gateway port.
This is not desirable behavior in many environments as the Parallels RAS Farm should only allow connections from users using the Parallels RAS Client and not a traditional RDP Client (MSTSC).
Disabling tunneling policies will restrict RDP access through the RAS Secure Client Gateway port.
The main reason for disabling tunneling policies from a security perspective is to prevent a DDOS attack.
From Parallels RAS v17.x any new installations have tunneling policies disabled by default. For customers upgrading from a previous version it is recommended that this is disabled via the Parallels RAS Console manually.
To disable tunneling polices for the Parallels RAS Secure Client Gateway, launch the Parallels RAS Console. Select the Farm tree entry and then the Gateways section.
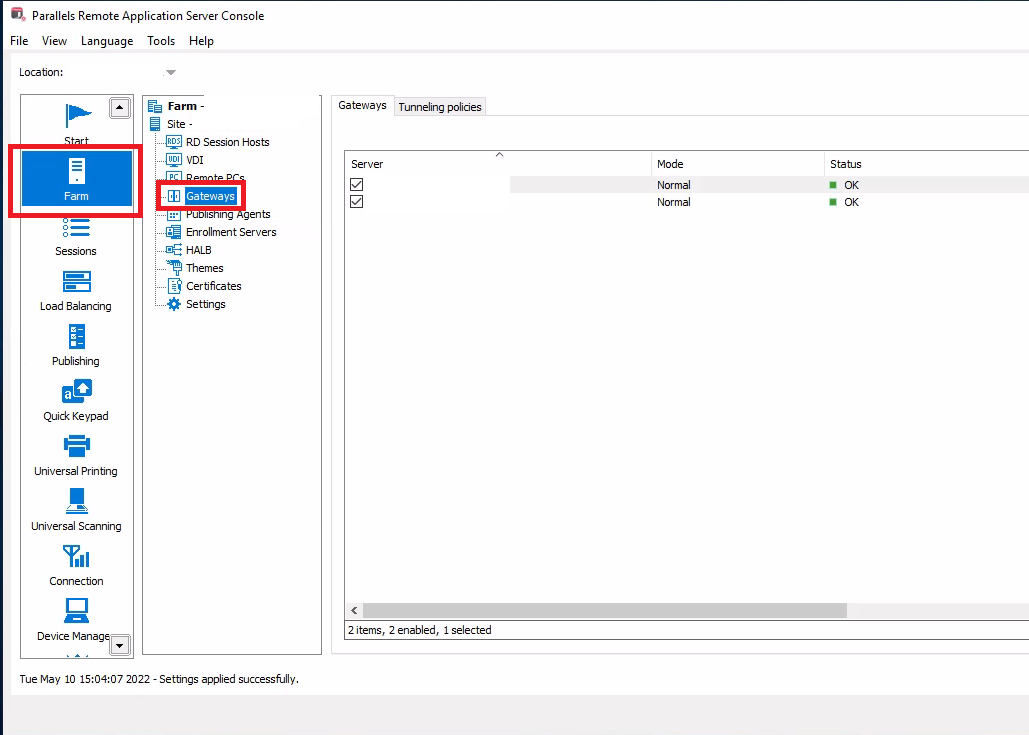
Select the Tunneling policies tab, right click the default policy and select Properties.
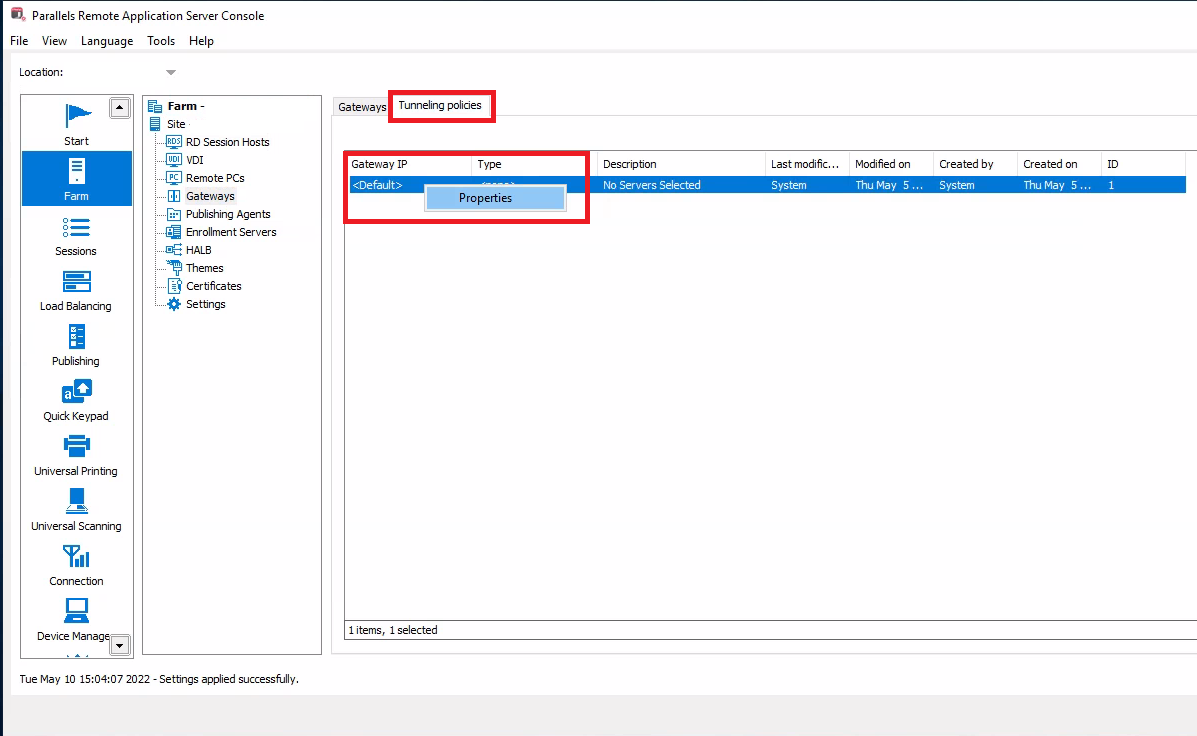
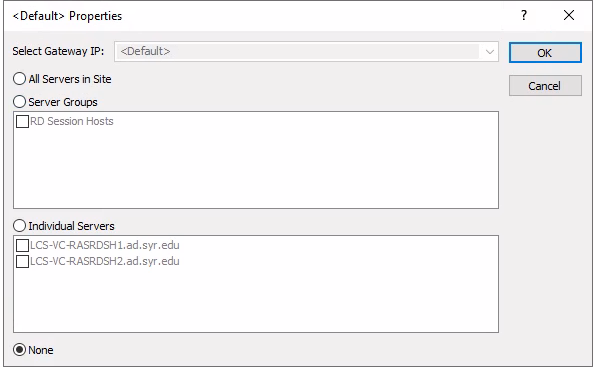
Ensure the None option is select and click OK.
User Permissions
Logging in remotely requires users to have remote access rights to the remote server. This can be carried out from Group Policy Management Console (GPMC), which is an administrative feature that can be installed via Server Manager or through PowerShell as described at https://technet.microsoft.com/en-us/library/cc725932(v=ws.11).aspx
Once GPMC is opened, navigate to Computer Configuration / Policies / Windows Settings / Security Settings / Restricted Groups. Right-click on Restricted Groups and click on Add User Group that should have access to log in on to the remote machine (RDSH Server, Remote PC, VDI).
More information on how to add Domain Users/Group to the Remote Desktop Users group via Group policy can be found at https://technet.microsoft.com/en-us/library/cc725932(v=ws.11) .
User session limit
Restrict users to a single Remote Desktop session
This Group Policy setting will restrict each user to a single session (either active or disconnected) on that server. If the user leaves the session in a disconnected state, the user automatically reconnects to that session at the next logon.
It is recommended that this option be enabled in order to prevent users from creating multiple sessions and using extra server resources. It will also ensure that when using Parallels RAS published applications that all applications are run within the same user session instance.
This policy option is located under the Computer Configuration \ Polices \ Administrative Templates \ Windows Components \ Remote Desktop Services \ Remote Desktop Session Host \ Connections section of the Group Policy Management Editor.
Session time limits
There are several Group Policy settings that control user session timeouts depending on state.
These policy options are located under the Computer Configuration \ Polices \ Administrative Templates \ Windows Components \ Remote Desktop Services \ Remote Desktop Session Host \ Session Time Limits section of the Group Policy Management Editor.
Set time limit for disconnected sessions
This policy controls the length of time an active but disconnected session remains open. Once the defined time limit is reached the session is ended (logged off) automatically.
It is recommended that this option is enabled and configured with the preferred time limit. This will prevent disconnected sessions from consuming server resources.
Set time limit for active but idle Remote Desktop Services sessions
This policy controls the length of time that an active Remote Desktop services session can be idle before it is automatically disconnected. By default, Remote Desktop Services allows sessions to remain active but idle for an unlimited amount of time.
It is recommended that this option is enabled and configured with the preferred time limit.
Set time limit for logoff of RemoteApp sessions
This policy controls the length of time a RemoteApp session will remain in a disconnected state (after a user closes all RemoteApp programs) before the session is logged off.
Parallels RAS does utilise some of the RemoteApp functionality available within Remote Desktop Services. Parallels RAS published applications are affecting by this policy setting.
It is recommended that this option is enabled and configured with the preferred time limit.
Additional Polices
The ‘Set time limit for active Remote Desktop Services sessions’ and ‘End session when time limits are reached’ polices can also be defined if required but are optional.
The ‘Set time limit for active Remote Desktop Services sessions’ policy option controls the maximum amount of time that a Remote Desktop Services session can be active before it is automatically disconnected.
The ‘End session when time limits are reached’ policy option defines if a Remote Desktop Services session that has timed out is ended (logged off) rather than disconnected. Obviously when linked with the previous options recommend above, even if the session remains in a disconnected state it will be ended (logged off) once the time limit for disconnected sessions is reached.
User environment lock down
There are many Group Policy settings that can control and lock down various aspects of a Remote Desktop Services desktop session, for example disabling control panel items, disabling registry modifications, removing options from Windows Explorer and controlling Windows Start menu behavior.
One of the most common and recommended configuration options is to hide the Remote Desktop Services host local hard disk drives.
Hide specified drives in My Computer
This policy setting controls which drives are visible to a user in Windows Explorer / My Computer.
This policy option is located under the User Configuration \ Polices \ Administrative Templates \ Windows Components \ File Explorer section of the Group Policy Management Editor.
It is recommended that at least the A, B and C drives are restricted. If the Remote Desktop Services host also has a D drive which is used by the system itself to store applications or content, this can also be hidden if required.
Hiding the local drives from the user will help to prevent the users saving or storing data on the Remote Desktop Services host’s local hard drives.
The User Configuration \ Polices \ Administrative Templates \ Windows Components \ File Explorer section also contains many other options to control the behavior and visibility of options within the Windows Explorer interface/context menus. For example, the ‘Remove Map Network Drive and Disconnect Network Drive’ policy will remove the options from Windows Explorer to map and disconnect network drives.
Although these additional policy options are not covered within this article, it is recommended that the organization review the available and additional polices to configure the Remote Desktop Service Hosts as required.
Managing Reporter database
To avoid space issues with the database, administrators should configure how long Session Information and Server Counters Information should be stored in the database.
On the Administration > Reporting tab page, click the Tracking Settings button. The Advanced Setting dialog opens.
In the Session Information section, specify the following options:
Enable Tracking. Records sessions data (affects all reports except server reports).
Retain information for. Select for how long the information should be kept in the database.
In the Server Counters Information section, specify the following:
Enable Tracking. If selected, server counter data is recorded (affects server reports only).
Retain information for. Select for how long the information should be kept in the database.
Track CPU / Memory counter when change is more than (%). Use these two options to set the minimum CPU and Memory resource usage required to record data.
More information can be found in the RAS Administrator's Guide.
