Creating SAML Attribute Mappings
To use SAML attribute mappings, an additional update to your AppsAnywhere servers is required.
It is recommended to read SAML 2.0 Common and SAML Attribute Mapping to configure the identity provider before proceeding.
Overview
Much like LDAP Importing directory entities, SAML attribute mappings can be created on the Directory Mappings page. This allows for mapping roles to arbitrary SAML attribute names and values, as well as being able to use these records in all other places that LDAP records can be found - such as in Provisioning and Delivery Method Restrictions.
Creating Mappings
To create an attribute mapping, navigate to the Directory Mappings page as shown below.
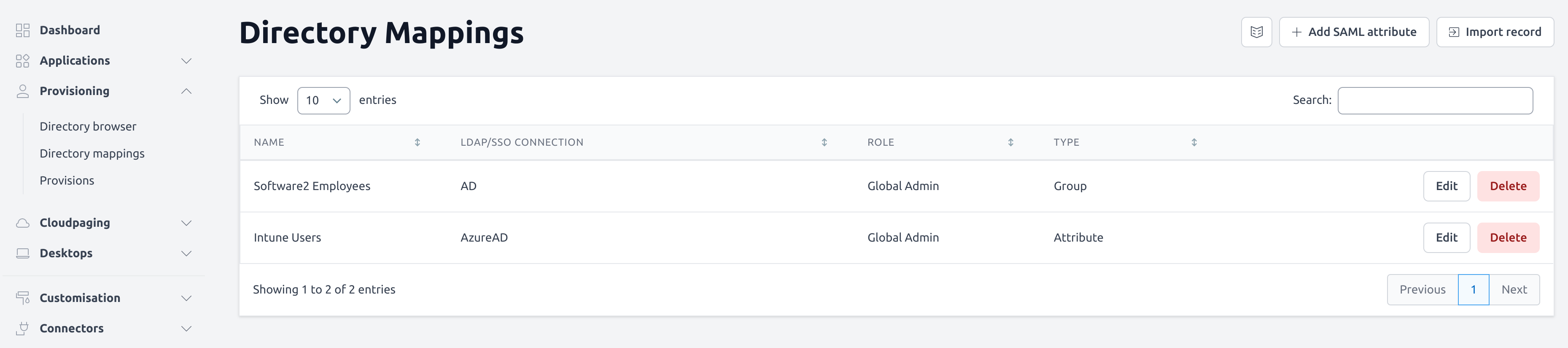
Click on the Add SAML attribute button in the top right
Fill out the form using the attribute name and value you wish to map to users
The Connection Key field will allow you to choose from your list of SAML SSO methods (see SAML 2.0 Common for more information on setting these up) to determine when this attribute will be used
More information on these fields can be found in the table below
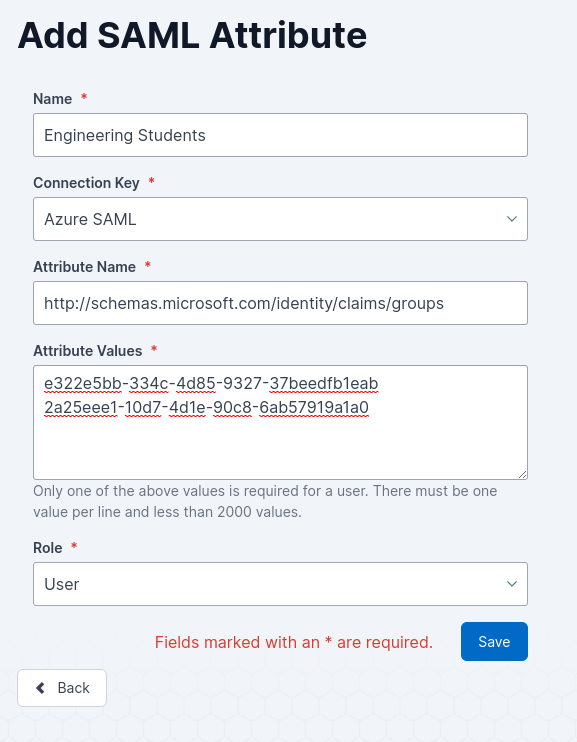
4. Click Save.
Directory Mapping Settings
Field Name | Description | Intended Value |
|---|---|---|
Name | A display name used for this mapping, in some scenarios this may be the only visible information you will have to differ between mapings. We suggest using a name you will recognise and understand the purpose of the mapping. | An understandable value for the attribute values used, e.g. Engineering Students |
Connection Key | This will be a list of your existing SAML SSO methods, this will determine which logins will have the attributes attempt to be matched for. | The SAML method users will attempt to match attributes for. |
Attribute Name | The name of the attribute that will be matched against the user’s login details. | The SAML-compliant attribute used to retrieve the information, e.g. http://schemas.microsoft.com/identity/claims/groups |
Attribute Values | The values of the attribute to match against the user’s login details, with a limit of 2000 values per attribute. Only one of the values is required to match. Each value should be on a different line. | The values to be matched, e.g. 2 groups related to engineering e322e5bb-334c-4d85-9327-37beedfb1eab |
Role | This determines the level of access that a user linked to that attribute will have to AppsAnywhere.
| The desired role of the user, e.g. User |
