SAML Attribute Mapping
Attribute Mapping Settings
To use SAML attribute mappings
An additional update to AppsAnywhere servers is required
SAML 2.0 Common must be completed
These settings control the sources of the attribute values that are required for SAML logins. As SAML can be used in conjunction or without an LDAP connection, there are some quick-start options that will fill out the fields with some basic information that may help in these scenarios.
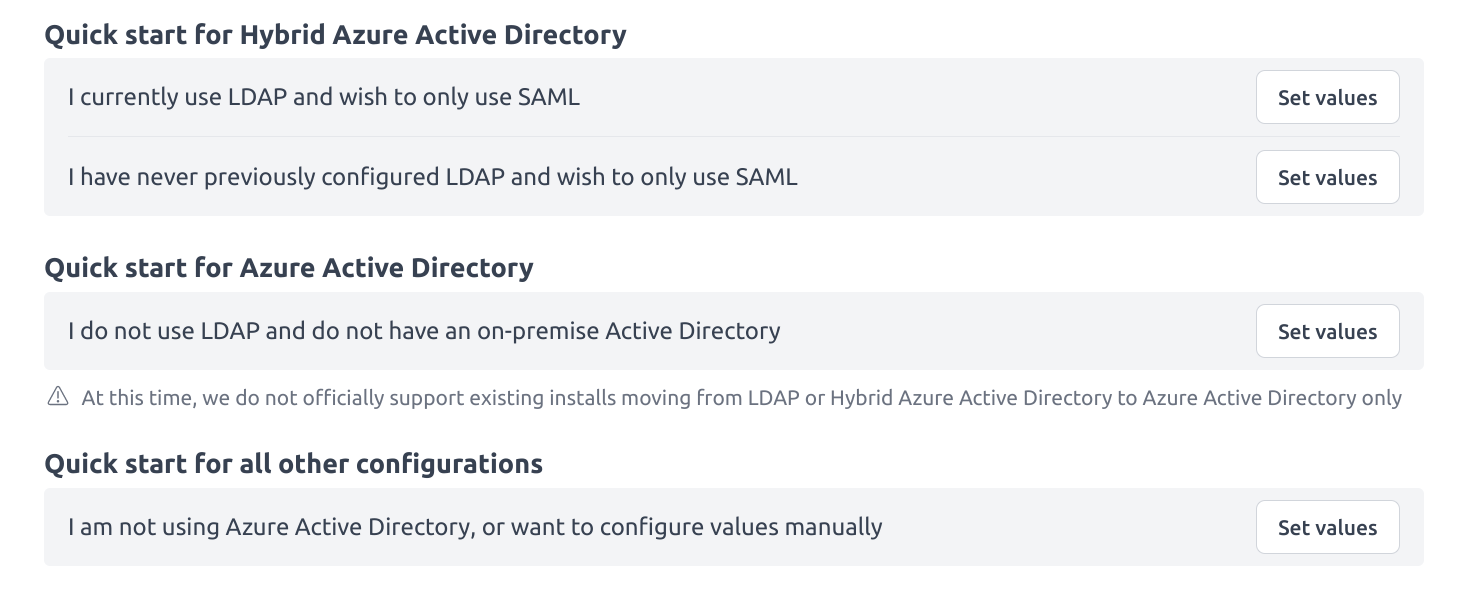
When using SAML only (without an LDAP connection)
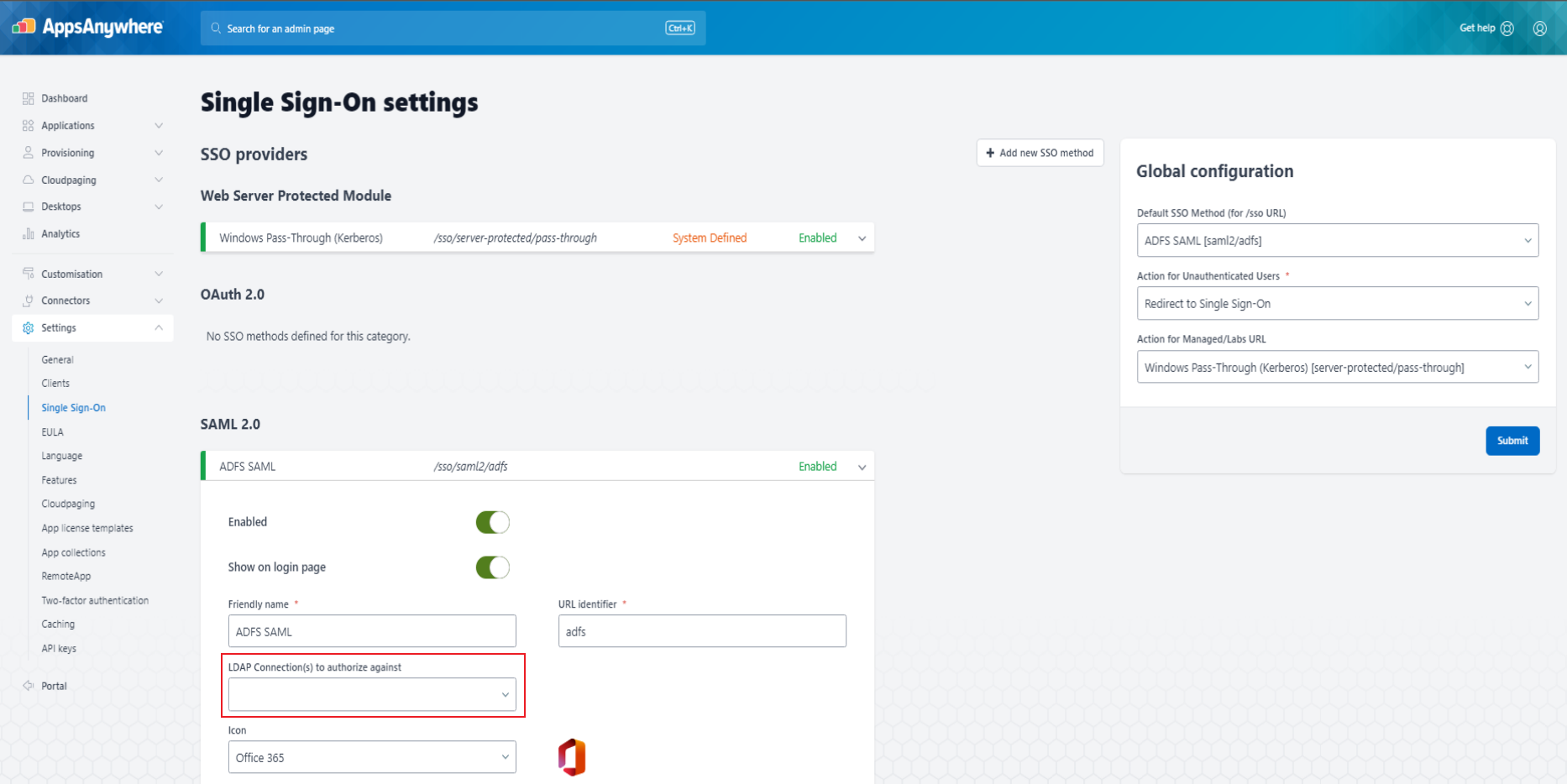
LDAP Connection(s) to authorize against should be blank/removed
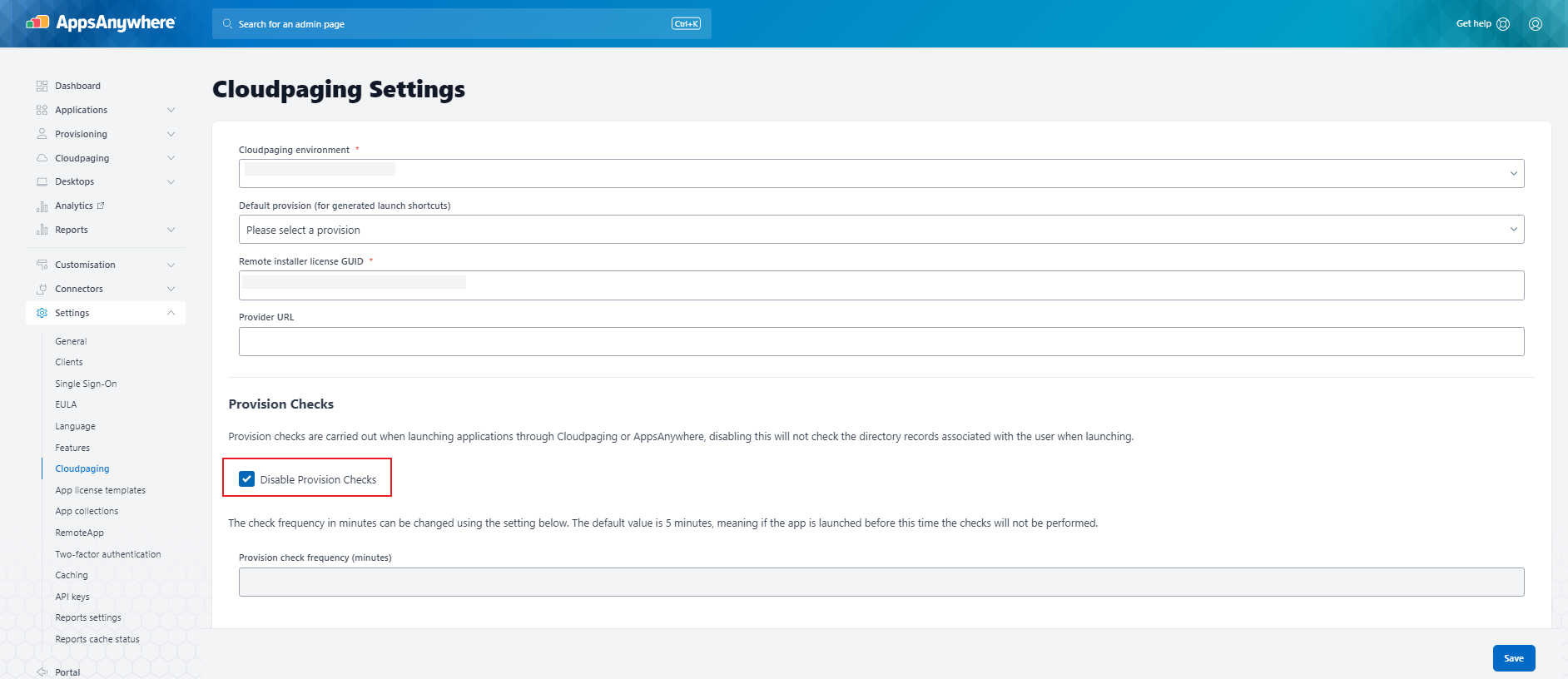
Disable Provision Checks should be checked in Cloudpaging Settings
End users will be unable to login until Creating SAML Attribute Mappings has been completed
Values automatically populated by the quick-start options are:
Quick-start Option | Fields populated | Value | Description |
|---|---|---|---|
Hybrid Azure Active Directory
| Encoding | Base64 | The encoding value is changed from None to Base64. This is based on the User Unique ID Attribute value mapped to the user.onpremiseimmutableid property which is Base64 encoded. The user.onpremiseimmutableid returns the users on premise Active Directory Immutable object ID value which AppsAnywhere can use to match previously stored information. This ensures that when transitioning from LDAP to SAML, user profile information amongst other settings are retained. |
User Principal Name Attribute | Default claim added automatically when configuring an AzureAD Enterprise application with SAML Single Sign On. | ||
User Display Name Attribute | Default claim used in certain situations. There are a limited number of situations where a claim using this namespace URI and user.displayname source attribute will be pre-configured. It is advised this value and claim/attribute is checked, if not present by default, it will need to be defined. | ||
Hybrid Azure Active Directory
OR: Azure Active Directory
| User Unique ID Attribute | http://schemas.microsoft.com/identity/claims/objectidentifier | Default claim added automatically when configuring an AzureAD Enterprise application with SAML Single Sign On. |
Encoding | None | The encoding value is changed from None (which is the default) if not currently set. This is based on the User Unique ID Attribute using the default AzureAD claim http://schemas.microsoft.com/identity/claims/objectidentifier which the return value is not encoded. | |
User Principal Name Attribute | Default claim added by default when configuring an AzureAD Enterprise application with SAML Single Sign On. | ||
User Display Name Attribute | Default claim used in certain situations. There are a limited number of situations where a claim using this namespace URI and user.displayname source attribute will be pre-configured. It is advised this value and claim/attribute is checked, if not present by default, it will need to be defined. | ||
All other configurations | None | n/a | n/a |
The Quick Start for all other configurations option does not set any default values, however it will remove anything previously defined in the User Unique ID Attribute and Encoding fields.
Fields and populated values are removed if different quick start options are selected.
If the incorrect quick start option had been previously used, it is recommended to manually remove the populated values in the User Unique ID Attribute, User Principal Name Attribute and User Display Name Attribute fields before selecting a new quick start option.
The values populated when selecting one of the quick-start options may not work in all cases. These values should be reviewed to ensure they are correct based on the SAML configuration and provider.
See below for explanations on each field (some of the fields have been discussed in the previous section, however additional information is provided below).
Field Name | Description | Intended Value |
|---|---|---|
Domain Attribute | In order for AppsAnywhere to know which local domain the authenticating user is a part of, the name of a SAML attribute that contains this information may be provided. If multiple LDAP connections have been selected, there are two main scenarios where this would be the case:
See below for more information about federated domain aliases. NOTE: In the case where SAML only is used and the method has no associated LDAP connections, this field is mandatory. However if your IdP does not support or it is not possible to create a claim containing an attribute which contains the domain name, an arbitrary value can be provided. | The SAML-compliant attribute name in the SAML AuthnResponse containing the fully qualified domain name of the domain the user is part of, e.g. domain.edu Note: This must be the attribute name and not the friendly name |
Short Domain Attribute | The name of the SAML attribute made available to AppsAnywhere that the Short Domain can be retrieved from. NOTE: In the case where SAML only is used and the method has no associated LDAP connections, this field is mandatory. However if your IdP does not support or it is not possible to create a claim containing an attribute which contains the short (NetBIOS) domain name, an arbitrary value can be provided. However be aware that in this situation the a value must be defined in the Short Domain Fallback Value field (detailed below). | The SAML-compliant attribute name in the SAML AuthnResponse containing the short (NetBIOS) domain name of the domain the user is part of, e.g. shortdomain Note: This must be the attribute name and not the friendly name |
Short Domain Fallback Value | This is the default value of the short (NetBIOS) domain name if the attribute cannot be retrieved from the SAML AuthnResponse. | A default value for the short (NetBIOS) domain name e.g. MYDOMAIN |
User Unique ID Attribute | The name of the SAML attribute that is used as the unique user ID. This is used in pair with the Encoding field below. | The SAML-compliant attribute name in the SAML AuthnResponse containing the unique user ID, e.g. http://schemas.microsoft.com/identity/claims/objectidentifier Note: This must be the attribute name and not the friendly name |
Encoding | The encoding type of the User Unique ID Attribute field, this can either be None or Base64. Only set an encoding type if you are sure it is required. | None or Base64 depending on how the SAML attribute value is encoded. |
Username Attribute | To determine the identity of the user, the username should be made available to AppsAnywhere within the SAML AuthnResponse returned by the identity provider. The name of this attribute can be provided here so that during the authorization process AppsAnywhere can extract this information. Note: The Expected username format field must contain the correct syntax to match the format of the value this attribute will return. | The SAML-compliant attribute name containing the username in the SAML AuthnResponse, e.g. http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name Note: This must be the attribute name and not the friendly name |
User Principal Name Attribute | To determine the identity of the user, the name of the SAML attribute that is used to retrieve the User Principal Name value is also required. Note: This value maybe the same as previously defined in the Username Attribute field if you prefer to use the UPN as the defined username format. | The SAML-compliant attribute name containing the user principal name in the SAML AuthnResponse, e.g. http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name Note: This must be the attribute name and not the friendly name |
User Display Name Attribute | The display name of the user should be made available to AppsAnywhere within the SAML AuthnResponse returned by the identity provider. The name of this attribute can be provided here so that during the authorization process AppsAnywhere can extract this information. This is the display name your users will see on their AppsAnywhere profile. | The SAML-compliant attribute name containing the user’s display name in the SAML AuthnResponse, e.g. http://schemas.microsoft.com/identity/claims/displayname Note: This must be the attribute name and not the friendly name |
Federated Domain Aliases | In the event your users authenticate using a federated domain alias (i.e. the domain name portion of their login does not have a represented domain within your infrastructure) and only a single LDAP connection has been selected, a value for this field will be required in order for AppsAnywhere to know that this part of their login is not a real domain. Note: This field is not required or used when no or more than one LDAP connection is selected. Any federated domain values specified in this field will be ignored in this case. Domain aliases can also be specified on the LDAP connection itself. | A list of valid domain names that corresponds to the federated aliases used in your user's usernames, e.g. myalias.com If the domain found in the username matches this set value, then it will be ignored, and the domain associated with the selected (single) LDAP connection will be used instead. These should be seperated by semi colons, e.g. myalias.com;anotheralias.com |
When using SAML only (without an LDAP connection)
LDAP Connection(s) to authorize against should be blank/removed
Disable Provision Checks should be checked in Cloudpaging Settings
End users will be unable to login until Creating SAML Attribute Mappings has been completed


To configure SAML attribute mappings for end user access, follow Creating SAML Attribute Mappings
