Using Windows Pass-Through (Kerberos) Authentication
It is recommended to configure SAML 2.0 Single Sign On rather than Kerberos. SAML is compatible with all device types and reduces the need to manage multiple SSO methods.
Introduction
By default AppsAnywhere presents all users with a web based login page.
Integrated Windows Authentication can also be used to allow Single Sign On (SSO) from domain machines using Kerberos. To initiate SSO automatically, you can direct users on domain machines to the following URL: https://appanywhere.uni.edu/labs
Our recommended approach is to use this URL when creating shortcuts to the AppsAnywhere portal for end-users on managed Windows devices.
You can then easily disable first-time user prompts for SSO in AppsAnywhere General Settings.
Note
This is presuming you have already completed a Managed Deployment of AppsAnywhere Client and Cloudpaging Player to domain joined devices.
From Load Balancer Configuration; all traffic sent to the backend servers from the load balancer MUST be over HTTPS/443 for Kerberos to function.
Classrooms
In a classroom environment you may also want to suppress all user prompts including the first time welcome tour and EULA.
This is to avoid students getting a slightly different experience at the start of class, which can be off-putting for tutors. To do this direct users to the special URL of: https://appanywhere.uni.edu/labs
Other SSO Methods
AppsAnywhere also supports a range of additional SSO methods for web based Single Sign On. Please refer to Single Sign On Settings for these options.
This article is focused on configuring SSO for domain joined Windows machines.
Configuring for SSO with Integrated Windows Authentication
For SSO to work on domain Windows devices using Kerberos, the following need to be in place:
Your AppsAnywhere appliance must be Configured for Single Sign On
SPN records must be created for your AppsAnywhere service account (also via the above link).
Single Sign On must be enabled in AppsAnywhere Admin Settings > Single Sign On
The Active Directory user must be imported, or be a member of an imported AD group
The user is logged in to a domain machine with their AD account.
The user is running one of the latest versions of Edge or Internet Explorer*
Internet Explorer is configured for automatic login either locally in Internet Options or via GPO (this is sometimes referred to as pass-thru authentication)
The user visits one of the above special URLs
*It is also possible to configure SSO with Google Chrome and most other browsers. We have provided some details on how to test this below but you may need to refer to the publisher for details of how to apply global browser settings in your environment.
AppsAnywhere Single Sign On Settings
As noted above; Single Sign On must be enabled in AppsAnywhere Admin Settings > Single Sign On.
However, we recommend that you leave the Action for Unauthenticated Users set to Redirect to Login. Otherwise AppsAnywhere will attempt SSO even when users visit your normal service URL (e.g. https://appanywhere.uni.edu).
The above is not normally desirable, as users on BYOD devices will never be able to use Integrated Windows Authentication for SSO.
Configuring your browser for testing Integrated Windows Authentication
Microsoft Edge
Procedure
Verify that you are logged into Windows as a user in the domain.
Update Internet Options.
Use Windows Search and open Internet Options
Navigate to the Security tab.
Select Local Intranet
Click Custom level.
Select Automatic login only in Intranet zone.
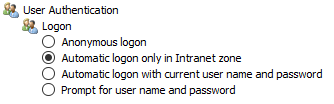
Click OK.
Verify that the AppsAnywhere domain is part of the local intranet zone.
In the Internet Options dialog box on the Security Settings tab with Local intranet still selected, click Sites.
In the Local intranet dialog box, click Advanced.
In the next dialog box (also titled Local intranet), type the URL of your load balanced address (e.g. https://appanywhere.uni.edu) in the Add this Web site to the zone box, and then click Add.
In the Local intranet dialog, box click OK.
In the original Local intranet dialog box, click OK.
In the Internet Options dialog box, click OK.
Firefox
Procedure
In the URL text box of the Firefox browser, enter about:config to access the advanced settings.
Click I'll be careful, I promise!.
Double-click network.negotiate-auth.trusted-uris in the Preference Name column.
Enter your AppsAnywhere Service URL in the text box. e.g. https://appanywhere.uni.edu
Click OK.
Double-click network.negotiate-auth.delegation-uris in the Preference Name column.
Enter your AppsAnywhere Service URL in the text box e.g. https://appanywhere.uni.edu
Click OK.
Test Kerberos functionality by using the Firefox browser to log in to login URL e.g. https://appanywhere.uni.edu/labs
Chrome
To make SSO work in Google Chrome, configure Internet Explorer using the method described above (Chrome uses IE setting).
In addition, it should be noted that all new versions of Chrome automatically detect Kerberos support on the website.
If you are using one of the earlier Chrome (Chromium) versions, run it with the following parameters to make Kerberos authentication on your web servers work correctly:
--auth-server-whitelist="*.software2.com"--auth-negotiate-delegate-whitelist="*.software2.com"
For example:
"C:\Program Files (x86)\Google\Chrome\Application\chrome.exe” --auth-server-whitelist="*.software2.com " --auth-negotiate-delegate-whitelist="*.software2.com"
Finally, test Kerberos functionality by using the Firefox browser to log in to login URL e.g. https://appanywhere.uni.edu/labs
If the Kerberos authentication is successful, the test URL goes to the Web interface.
Deploy to managed devices
Deploy the above internet settings to managed devices using Group Policy
Ensure all managed devices load AppsAnywhere SSO on login using the configured URL e.g. https://appsanywhere.uni.edu/labs
